Although the marine industry has a long history of success in risk management, cyber threat actors represent a different kind of menace. They are sophisticated, constantly evolving, and highly motivated.
Jones Walker LLP have just released the findings of its 2022 Ports &Terminals Cybersecurity Survey, noting that cyber attacks are on the rise at US ports & terminals
An overwhelming majority (95%) of port and terminal respondents indicated they believed that their industry is “very” or “somewhat” prepared for any cybersecurity threat. A similarly large majority (90%) reported that their own facilities and organizations are “very” or “somewhat” prepared to withstand a cyber-breach incident.
Despite this level of confidence, keeping pace with the increasing prevalence of cyber attacks remains a significant challenge. 74% of respondents indicated that their systems or data had been the target of a breach or breach attempt within the past year.

Take a Clear-Eyed View of Potential Threats
Survey participants identified “lone wolf” hackers and organized crime groups as the top threat actors menacing the ports and terminals sector, with nation-state affiliated groups a close third. Still, 35% listed internal staff and employees as a threat. These figures line up with findings in the broader economy.
This perception also aligns with stakeholder experience. Of the respondents who reported being victims of cyber breaches, 64% indicated a solo threat actor/hacker was responsible, while 32% identified an organized crime group.
Need to know more about cybersecurity at sea?

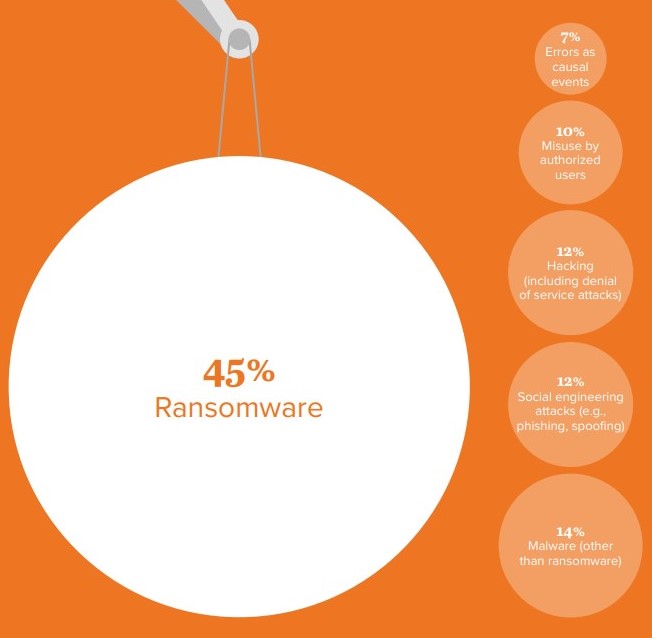
Fear of ransomware appears to be outpacing actual ransomware events, as only 20% of respondents whose organizations had actually been victimized by a cyber attack listed ransomware as the primary attack vector.
Make a Plan, Test the Plan, Update the Plan
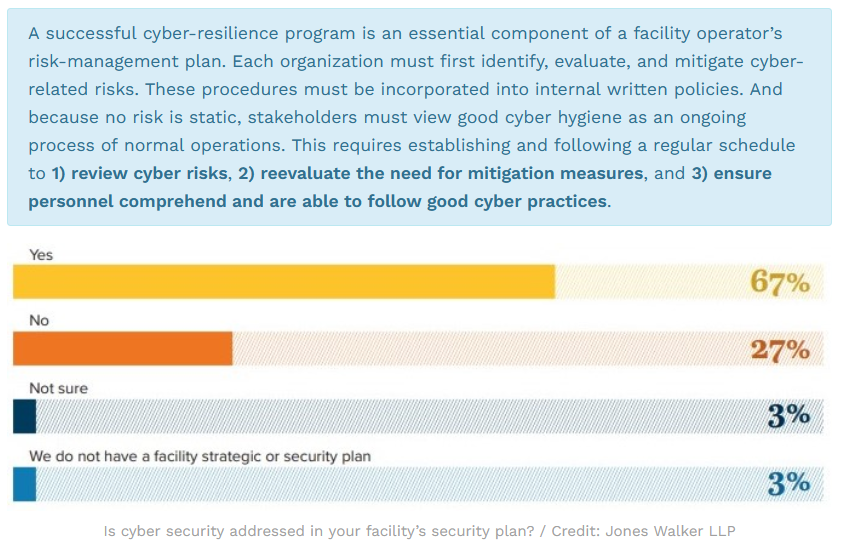
Port and terminal respondents reported a high level of cybersecurity planning. Nearly three-quarters (73%) indicated that they have in place written IRPs and cybersecurity plans separate from their USCG-reviewed and approved FSPs, and 23% reported that their cybersecurity plans are incorporated into their facility strategic or security plans.
But having a plan and having a plan that works are two different things. To be effective, stakeholders must ensure that facilities’ plans are practical, sufficiently detailed and comprehensive, and updated and tested frequently.
People and Communication Are Key
Although the marine industry has a long history of success in risk management, cyber threat actors represent a different kind of menace. They are sophisticated, constantly evolving, and highly motivated.
Despite their sophistication, however, some of the most important defenses are among the simplest to implement and manage. Strong password-management protocols, restrictions on the use of unsupported software and personal mobile devices, and robust training can establish a solid, frontline defense, which in turn can be supplemented by higher-level, technology-based solutions where resources allow.
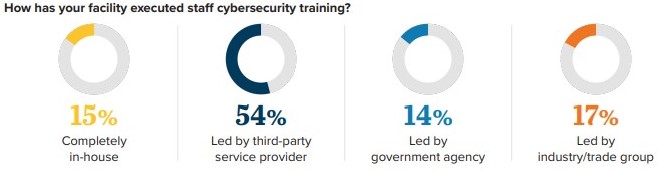
Regular, effective employee training is particularly critical to a successful risk-mitigation strategy. Cybersecurity training should be provided on an annual basis, at a minimum, and more often for key employees whose responsibilities include managing highly sensitive data or systems. Without regular instruction and reinforcement, learning fades quickly.
When asked about the frequency of cybersecurity training, there was a significant difference between the responses of blue- and brown-water facility stakeholders. This annual standard was met by 57% of the blue-water respondents, but by only by 25% of the brown-water respondents.
Source: Safety4Sea









